Network VAPT
Let us secure the Security And Reliability Of Your Network by Conducting A Comprehensive Network VAPT (Vulnerability Assessment And Penetration Testing).
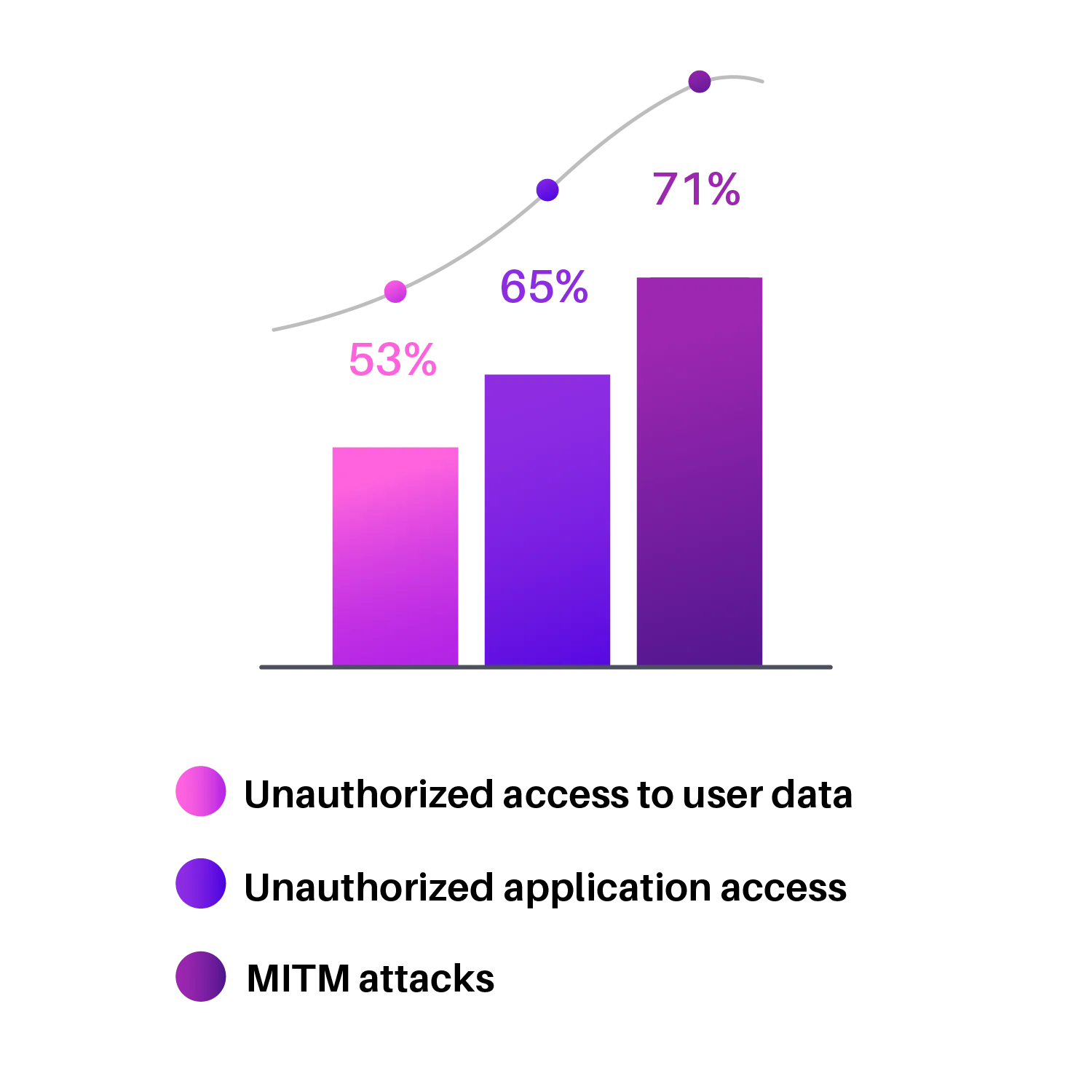
In 2023, cyber attacks will happen every 11 Sec!
Get authentic VAPT results with our comprehensive Network VAPT and skip the hassle of the traditional agency hunting process, proposal submission, consulting, to-and-fro negotiations, etc.

Our Research
What is Network VAPT and why your Enterprise needs it?
A network comprises the backbone of an organization through which all the data keeps transmitting. Hence, it is critical aspect to secure your components as well as systems and servers in your network and assure data privacy and its availability and integrity.
The Network Vulnerability Assessment will help the organization to be aware and gain knowledge about the risk and threats based on the environment. At the same time, the Network Penetration test will attempt to break through the vulnerabilities found and determine any possibility of malicious activities or unauthorized access.
In this context, network testing must address how to determine the correctness of a collection of tested network components, combined in a range of configurations.
This is but limited to the scope of technical IPs included in the entire network.
Our experts differentiate and suggest assessment methodologies and processes based on business requirements and network architecture.
Steps To Follow
Stages of Network VAPT
Discovery – Various methods do discovery of the Host. Then different ports are scanned for any vulnerabilities.
Assessment – Vulnerability assessment through service fingerprinting. Then the vulnerabilities are researched and checked through cross-referencing.
Exploration – This step is formulated to totally create a hacker-like situation and resolve it. The possible attacks and attack vectors are used to show how the system lacks the required strength.

We Believe In Transparent Pricing
Powering your business with world-class Network VAPT services.
Our Scope
Scope of Network Penetration Testing
- Information gathering
- Identify live host
- Identify OS type
- Perform vulnerability scanning
- DoS services
- Web scan services
- SSL scans on all ports
- TCP UDP scans
- Audit SSL
- Self-signed certificate
- SSL version 2 and 3 detection
- Weak hashing algorithm
- Use of RC4 and CBC ciphers
- Logjam issue
- Sweet32 issue
- Certificate expiry
- Openssl Change Cipher Sec issue
- POODLE vulnerability
- Openssl heartbleed issue
- Perform fingerprinting
- Identify hosts and footprint
- Find insecure databases and components
- Network port scanning
- Exploit vulnerabilities
- Find insecure services
- Hunting Common ports
- DNS (53) UDP, SMTP (25) TCP
- SNMP (161) UDP, SSH (22) TCP
- Cisco VPN (500) UDP
- SMB (445,137,139) TCP
- FTP (21) TCP
- Telnet (23) TCP
- RPC (111) TCP/UDP
- NTP (123) UDP
- HTTP/HTTPs - (443,80,8080,8443) TCP
- SQL Server (1433,1434, 3306) TCP
- Oracle (1521) TCP
Expert cyber-security solutions, at Tailor-made costing
That fit every requirement
Experts strategy
Why Network Pen testing?
One of the major benefits of Network VAPT is that it will help you in gaining valuable insight into the in-scope assets’ security posture and be able to fix them before hackers can seriously damage them by exploiting the same. Network security testing is important for any corporate to protect its intellectual property and also important because networks are hard to build correctly, and even networks that appear to work most of the time may have subtle bugs that require intermittent action.
The network pen testing problem is especially hard because networks are dynamic. The component network elements change. The configuration of a given network element may also change. The connectivity of the network may change because components enter and leave; it may also change because of failures.
In this context, network pen testing must address how to determine the correctness of a collection of tested network components, combined in any of a range of configurations. It is highly advised to get a VAPT done from one of the top cyber security companies or the best network security company.

Network VAPT process



IP (Network) Pen-Testing
How is IP/Network VAPT different from IT security Audit?
In IT infrastructure audits, detailed analysis of the current architecture, internal security of system components, current policies and other infrastructure related parameters are considered and performed by using a phased approach for overall information security of the organization.
Any Query?
Frequently Asked Questions
Our executive will provide you an Questionnaire, which asks some details of your network like IPs, Server details etc. These details you need to provide in order to start the assignment.
Network VAPT is the process of finding vulnerabilities and pen-testing the Network from the given set of IPs. Network Audit comprises of audit of all network components, security policies, end point hardwares and other network infrastructures which will help assess your risk and ensure security measures.
Yes, Invesics is an ISO 27001 certified Company. Resources who will work on the assignments are CEH certified. Security Lead at Invesics is a double graduate having Masters degree in Cyber Security and Incident Response.
INVESICS is ISO 27001 certified company and hence we have all the compliance applies to handle your data privacy. Further, you will get digitally signed NDA before starting the assignment, this NDA is legally valid.
In case of VAPT, you need to provide entire IP range for each location. In Network audit, you need to provide network diagrams depending on the locations.
You can convey that to you account manager, he will be there 24*7 to assist you. If your extra requirements does not fall under your selected plan, you will be given estimate for the extra work.
You can cancel the project anytime before signing NDA and you will get your money back. For more clarity, you can refer our refund policy here.
Relevant services
Supportive Cyber Security Services
Mobile Application Pen-Testing
Network Pen-Testing
Cloud Pen-Testing
Server Hardening
Under Attack? Need Immediate Assistance?
Reach out to our expert teammates to get solution for your Cyber Security concerns. We help to protect your organization from Data-breaches.