How to do VAPT?
Introduction
In the ever-evolving landscape of cybersecurity, businesses face constant threats from cybercriminals seeking to exploit vulnerabilities in their digital infrastructure. To safeguard your organization’s sensitive data and maintain customer trust, it is crucial to stay one step ahead of potential threats. This is where Vulnerability Assessment and Penetration Testing (VAPT) come into play. In this blog, we will explore the importance of VAPT and provide you with valuable insights on how to conduct an effective VAPT process.
Why VAPT Matters
Vulnerability Assessment and Penetration Testing serve as a powerful combination for identifying and addressing security weaknesses in your digital systems. A thorough VAPT process not only helps in identifying potential vulnerabilities but also validates the effectiveness of your security measures. By proactively addressing these weaknesses, you can prevent costly data breaches, mitigate reputational damage, and maintain compliance with industry regulations.
Understanding VAPT
Vulnerability Assessment (VA):
Vulnerability Assessment involves systematically scanning your digital environment to identify vulnerabilities, misconfigurations, or outdated software versions. By utilizing specialized tools and techniques, a comprehensive VA enables you to create an inventory of potential risks and prioritize them based on their severity. This initial step provides a solid foundation for the subsequent penetration testing phase.
Penetration Testing (PT):
Penetration Testing involves simulating real-world cyber attacks to exploit identified vulnerabilities and assess the effectiveness of your security controls. By emulating the tactics of potential adversaries, ethical hackers attempt to infiltrate your systems, identify entry points, and gain unauthorized access. The insights gained from PT help you understand the impact of a successful attack and implement targeted measures to bolster your defenses.
The Step-by-Step VAPT Process
Now that we have a clear understanding of VAPT, let’s delve into the step-by-step process of conducting an effective VAPT for your organization:
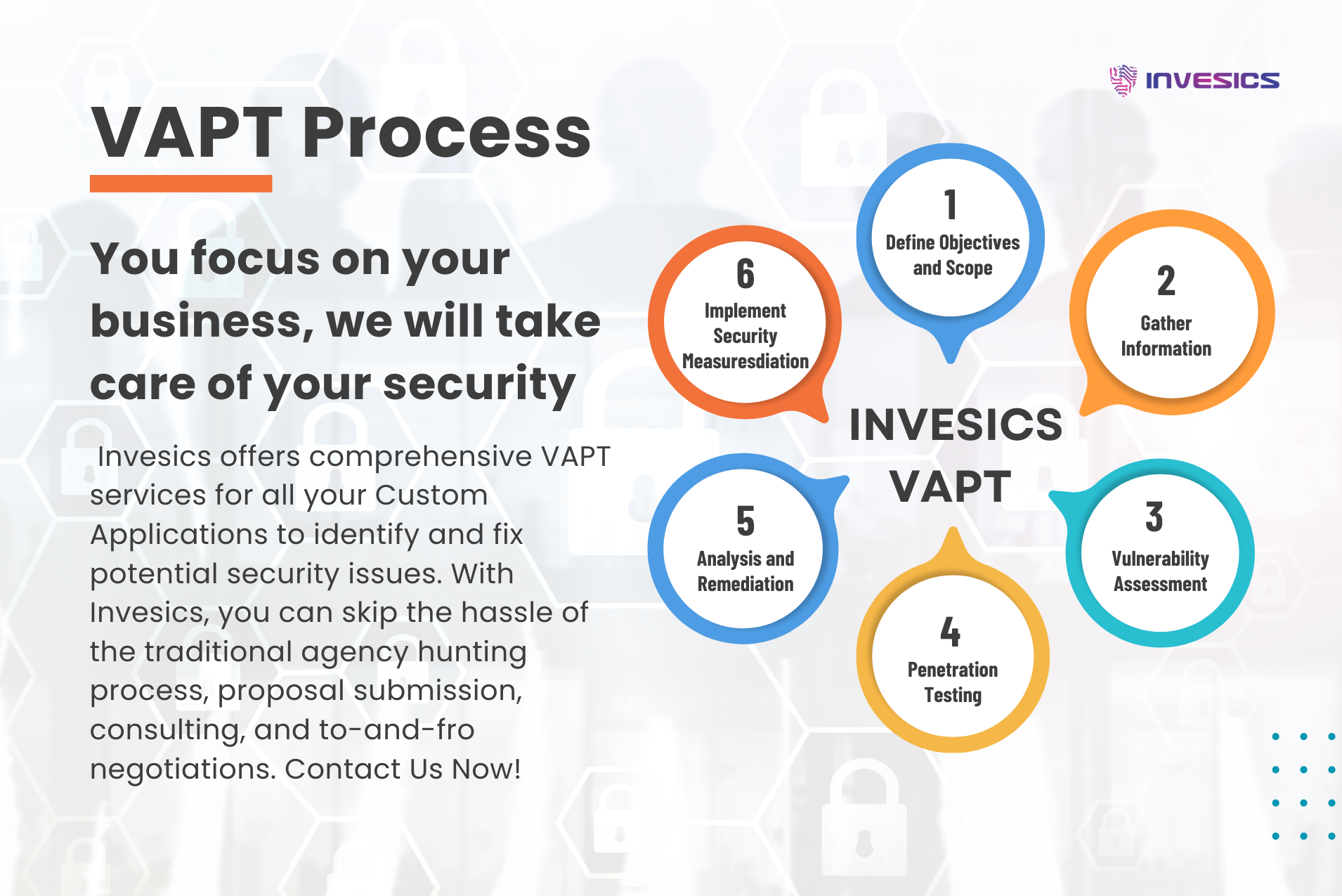

Define Objectives and Scope:
Clearly define the objectives and scope of your VAPT exercise. Identify the critical systems, networks, and applications that need to be tested. Consider involving all relevant stakeholders to ensure comprehensive coverage.
Gather Information:
Perform reconnaissance by collecting information about your digital assets. This includes identifying IP addresses, subdomains, software versions, and any other pertinent details that might aid in vulnerability identification.
Vulnerability Assessment:
Utilize automated scanning tools or engage a qualified cybersecurity firm, such as Invesics, to conduct a comprehensive vulnerability assessment. Analyze the results to identify potential risks and prioritize them based on their severity.
Penetration Testing:
Engage ethical hackers or a professional penetration testing service, like the one offered by Invesics, to simulate real-world attacks. These experts will attempt to exploit identified vulnerabilities and provide detailed reports on their findings, along with recommendations for remediation.
Analysis and Remediation:
Thoroughly analyze the VAPT reports, identifying critical vulnerabilities and understanding the potential impact of a successful breach. Develop an action plan to address the vulnerabilities and prioritize remediation efforts based on the level of risk they pose.
Implement Security Measures:
Implement recommended security controls and measures to mitigate identified vulnerabilities. This may include patching software, improving network configurations, strengthening access controls, and educating employees about best security practices.
Conclusion:
In this digitized era, protecting your organization’s valuable assets is paramount. Vulnerability Assessment and Penetration Testing provide you with the necessary tools to stay one step ahead of malicious actors. By conducting a comprehensive VAPT process, you can identify and address potential security weaknesses, fortify your digital fortress, and ensure the safety of your critical data.
Remember, investing in VAPT is not a one-time affair. As technologies evolve and new threats emerge, regular assessments and tests are essential to maintain a robust security posture. Take charge of your organization’s cybersecurity by prioritizing VAPT as an ongoing practice. By doing so, you can stay proactive and protect your business from the ever-evolving threat landscape.
Additionally, partnering with a trusted cybersecurity company, like Invesics, can provide you with the expertise, tools, and support needed to conduct a successful VAPT process. With Invesics, you gain access to a team of skilled professionals who understand the intricacies of VAPT and can guide you through the process effectively. Trust Invesics to be your dedicated partner in securing your organization’s digital assets.
By considering these valuable insights and optimizing your VAPT process accordingly, you can enhance your organization’s cybersecurity posture and protect it from potential threats.

